The administrator configures load-balancing on each security appliance. The following are the steps to configure load-balancing for remote access VPN.
Asa Load Balancing Vpn And Aws Asa Vpn Configuration GET Asa Load Balancing Vpn And Aws Asa Vpn Configuration IN LOW PRICES. Cisco ASA Remote access VPN Load Balancing questions Hi, I have 3 5545 devices which will be used for SSL load balancing, however without encryption enabled the load balancing works fine. With the encryption I am getting duplicate address in SYSlog and also can see that its joining the cluster and dropping out. Shop for Cisco Asa Site To Site Vpn Configuration Step By Step And Asa Load Balancing Vpn Ads Immediately. Users require secured access to the workloads hosted in the cloud. Cisco Anyconnect VPN provides a secure way of accessing resources hosted in the cloud.
Step 1 Log in to the Cisco ASA using ASDM.
Step 2 On the main menu, choose Wizards.
Step 3 Choose the High Availability and Scalability Wizard.
Step 4 The High Availability and Scalability Wizard starts. The screen shown in Figure 12-69 is displayed. Click Configure VPN Cluster Load Balancing, as shown in Figure 12-69.
Figure 12-69 High Availability and Scalability Wizard
Figure 12-69 High Availability and Scalability Wizard
Step 5 Click Next.
Step 6 The screen shown in Figure 12-70 is displayed. Enter the cluster IP
address. The cluster IP address is the virtual address that VPN clients will use to connect to the cluster. In this example, the cluster IP address is 209.165.202.131.
Figure 12-70 VPN Cluster Load-Balancing Configuration
Figure 12-70 VPN Cluster Load-Balancing Configuration
Step 7 Enter a UDP port for load-balancing communication between all Cisco ASAs within the cluster. In this example, the default UDP port (9023) is used.
Step 8 Optionally, you can encrypt all VPN load-balancing traffic. Check the Enable IPsec encryption option to enable encryption.
Step 9 Configure a preshared secret. In this example, the preshared secret is 2wsx1qaz.
Step 10 The priority is set to 5. The higher the priority, the more commonly that this ASA will become the master of the cluster.
Step 11 The public interface is the outside interface in this example. The private interface is the inside interface, as shown in Figure 12-70.
Step 12 Click Next.
Step 13 A summary screen is displayed.
Step 14 Click Finish to apply the configuration to the Cisco ASA.
Example 12-13 shows the Cisco ASA remote access VPN and load-balancing CLI configuration.
Example 12-13 Cisco ASA Remote Access VPN and Load-Balancing Configuration hostname asa-1 !
interface GigabitEthernet0/0 description Outside interface connected to the Internet nameif outside security-level 0
ip address 209.165.202.129 255.255.255.0
interface GigabitEthernet0/1 description Inside interface connected to corporate network nameif inside security-level 100
ip address 10.250.10.1 255.255.255.0


interface Management0/0 nameif management security-level 0
ip address 10.250.30.1 255.255.255.0 management-only
!Split tunneling ACL
access-list IPSEC-RA-GROUP_splitTunnelAcl standard permit 10.250.10.0 255.255.255.0 !ACL to bypass NAT for remote access VPN connections access-list inside_nat0_outbound extended permit ip 10.250.10.0 255.255.255.0 10.250.50.0 255.255.255.0
!IP address pool for remote access VPN clients ip local pool IPSec-Pool 10.250.50.1-10.250.50.254 mask 255.255.255.0 !
!NAT configuration nat (inside) 0 access-list inside_nat0_outbound !
!RADIUS Configuration for remote access VPN authentication aaa-server RADIUS-Server protocol radius aaa-server RADIUS-Server (management) host 172.18.85.181 timeout 5 key cisco123
Asa Vpn Load Balancing Configuration Sheet
!Crypto map configuration crypto ipsec transform-setESP-AES-256-SHA esp-aes-256 esp-sha-hmaccrypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set transform-set ESP-AES-256-SHA
crypto map outside_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP crypto map outside_map interface outside continues
Example 12-13 Cisco ASA Remote Access VPN and Load-Balancing Configuration (Continued) !
!ISAKMP enabled on the outside interface crypto isakmp enable outside !ISAKMP policy for Remote Access VPN crypto isakmp policy 10 authentication pre-share encryption aes-256 hash sha group 5
lifetime 86400
!Load-balancing Configuration vpn load-balancing cluster key 2wsx1qaz cluster ip address 209.165.202.131 cluster encryption participate
!Remote Access Group Configuration group-policy IPSEC-RA-GROUP internal group-policy IPSEC-RA-GROUP attributes wins-server value 172.18.124.14 172.18.124.15 dns-server value 172.18.124.12 172.18.124.13 vpn-tunnel-protocol IPSec split-tunnel-policy tunnelspecified split-tunnel-network-list value IPSEC-RA-GROUP_splitTunnelAcl default-domain value companyc.com tunnel-group IPSEC-RA-GROUP type remote-access tunnel-group IPSEC-RA-GROUP general-attributes address-pool IPSec-Pool authentication-server-group RADIUS-Server default-group-policy IPSEC-RA-GROUP tunnel-group IPSEC-RA-GROUP ipsec-attributes pre-shared-key *
Was this article helpful?

Cisco Asa Vpn Load Balancing
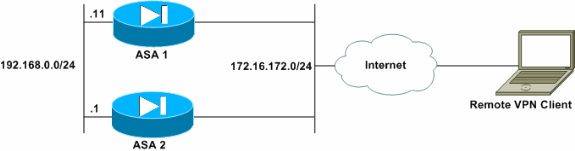
In these times that remote work is a must in most companies, IT teams need a fast and reliable way to improve and rapidly grow in remote access VPN capabilities.
One of the fastest ways to do that is to deploy Cisco ASAs with VPN load balancing. The Cisco ASA Family of security devices protects corporate networks and data centers of all sizes. It provides users with highly secure access to data and network resources – anytime, anywhere, using any device. Cisco ASA devices represent more than 15 years of proven firewall and network security engineering and leadership, with more than 1 million security appliances deployed throughout the world.
VPN Load Balancing is, as the name implies, a method to efficiently use system resources and achieve an increased performance in VPNs with the added availability. One of the biggest advantages of this solution is that VPN Load balancing is not dependent on the same model of Hardware, which means, to accelerate the process, we can always add more virtual ASAs, therefore we do not have to wait for delivery times, or space in the racks, or availability to have someone physically in the Data Center to install the box.
Either you already have one or two ASAs with remote-client configuration, which you want to enhance and increase the capabilities, or you want to set up a new configuration to allow the working from home environment, it is always possible to add new devices to the configuration.
Achieving higher performance in Remote Access VPNs as become more necessary than ever before, and Cisco continues to make it easy and manageable for customers and partners to augment and improve the capacity of VPN peers, so remote work does not feel so remote.
Tags:Cisco Asa Vpn Configuration Guide
