- Add Spf Record
- Spf Record Generator
- Spf Record Generator Microsoft Office 2016
- Spf Record Generator Microsoft Word
- Spf Record Creator Microsoft
- Spf Record Generator Microsoft Office 2010
So, does your domain have an SPF record and is it published to the Internet? If it has one, then what is it, and is it valid? Go to a website like mxtoolbox.com and run it through their validator. SPF records are DNS RRtype TXT records. The SPF-type is deprecated. The length of any TXT record has to be less than 255 octets between each set of. These tools are meant to help you deploy SPF records for your domain. They use an actual RFC 7208 compliant library (pyspf) for tests and will dynamically test for processing limit errors (no other testers I'm aware of do this).
SPF isn’t just for sunscreen. In the world of email, Sender Policy Framework or SPF is a method to validate that an email came from an authorized domain. In other words, it is a way to say that Postmark is allowed to send emails for your domain.
Learn more about using SPF to protect your domain from email spoofing.How SPF protects you? #
The SMTP protocol, the literal definition of email, has no protections on the From field in an email. As long as it’s a valid email address, there is no further validation. A malevolent actor can impersonate your bank, your employer, or anyone at all. This problem led to the creation of SPF.
SPF is a relatively recent solution. Different variations of the idea were proposed in the early 2000s, and these coalesced into the SPF specification as RFC 4408 in April 2006. SPF describes a DNS record in a special format to list all the domains allowed to send mail from the domain. This allows spam filters to easily check if the origin of an email is from an authorized domain.
Add Spf Record
Personally, I think it’s a rather elegant solution in that it uses existing architecture pieces, but it’s definitely not perfect. Using a special format for the TXT DNS record (which I’ll describe below) is non-standard but certainly is an easy way to gain adoption for a specification. The use of DNS for authentication isn’t without issues either. Despite the flaws of SPF, at Postmark we highly recommend users set up SPF in addition to DKIM. To paraphrase, we use the spam fighting tools we have, not the spam fighting tools we wish we had. From the Google Online Security Blog in December 2013, 89.1% of the non-spam email that Gmail received was authenticated by SPF and 74.7% was authenticated by both SPF and DKIM.
How SPF records work? #
At a high level, here is the workflow of how a mail server checks SPF:
- the Postmark server with IP address of 1.2.3.4 sends a message FROM joe@foo.com TO jill@bar.com
- the bar.com mail server gets the DNS records of type TXT for foo.com, looking for the SPF record
- the bar.com mail server compares the 1.2.3.4 IP address against the parts of the foo.com SPF record (described below)
- the message is accepted or rejected based on which part of the SPF record it matches
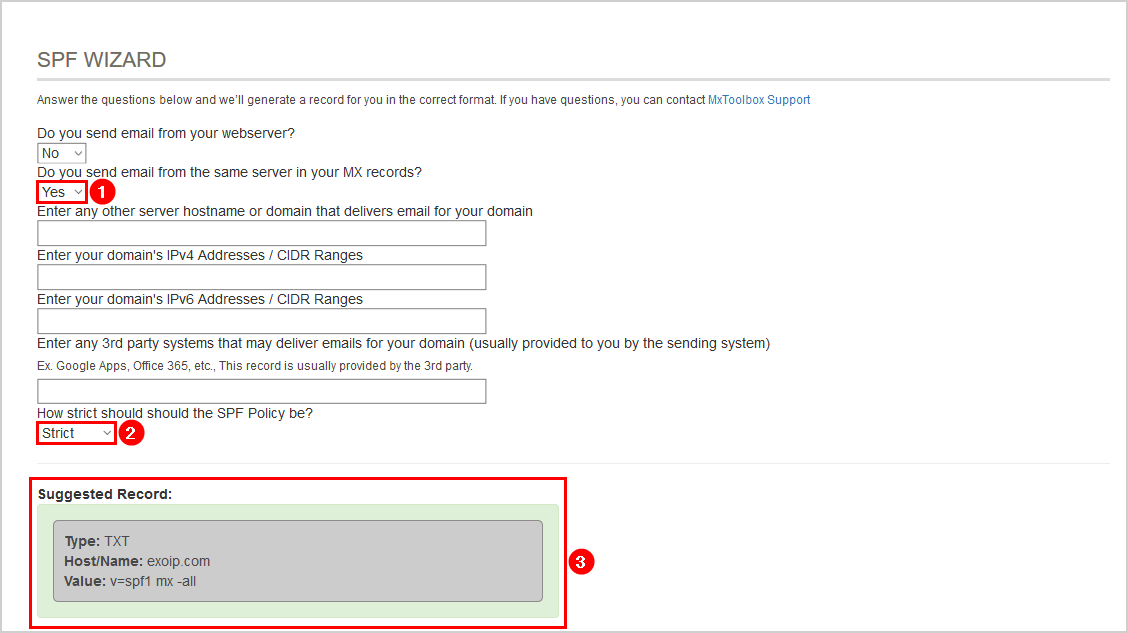
What SPF records mean? #
When you set up a sender signature in Postmark, we recommend you use the following SPF record:
Let’s break down what that means.
First thing to note is the syntax of the SPF record. It’s broken down into the version prefix and one or more mechanisms:
The version prefix is pretty simple. Since there can be multiple TXT records for a domain, this is the way to let parsers know that this is the record to be used for SPF checking. The mechanisms that follow are checked left to right and these specify different rules on how SPF is checked for the domain. The record that Postmark gives you has four mechanisms: a, mx, include:spf.mtasv.net and ~all. Before we go deeper into mechanisms, I need to explain qualifiers.
What are SPF qualifiers? #
The mechanisms can also be prefixed with a qualifier which describes the action to take when a sending IP matches the qualifier. The default qualifier is +. So the Postmark SPF record is the same as:
Spf Record Generator
Let’s go over what qualifiers are available.
+Pass, an IP that matches a mechanism with this qualifier will pass SPF.-Fail, an IP that matches a mechanism with this qualifier will fail SPF.~SoftFail, an IP that matches a mechanism with this qualifier will soft fail SPF, which means that the host should accept the mail, but mark it as an SPF failure.?Neutral, an IP that matches a mechanism with this qualifier will neither pass or fail SPF.
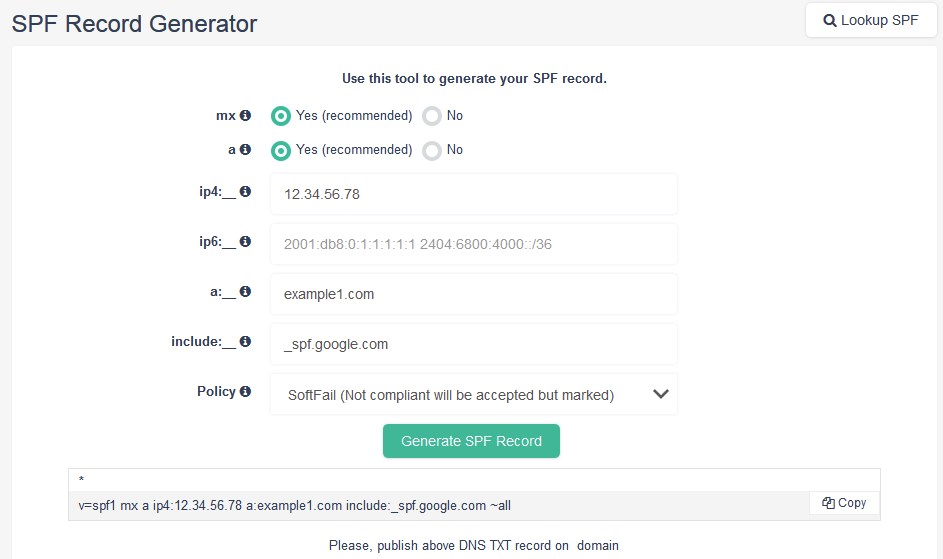
What are SPF mechanisms? #
The “a” mechanism #
Spf Record Generator Microsoft Office 2016
Let’s say that I send mail from IP 1.2.3.4 for the domain “example.com”. If “example.com” has an A record that returns 1.2.3.4 then this mechanism will pass.
The “mx” mechanism #
Any domain that hosts email has one or more MX records. These records define which email servers should be used when relaying email. For instance, when using Google Apps you insert several MX records into DNS. By including the “mx” mechanism, it automatically approves these servers and avoids you having to list them individually. This also avoids maintaining the list if they change later.
The “include” mechanism #
Let’s say that I send mail from IP 1.2.3.4 for the domain “example.com”. If the SPF record for “example.com” includes spf.mtasv.net and 1.2.3.4 passes against the SPF record for spf.mtasv.net then this mechanism will pass.
The “all” mechanism #
Spf Record Generator Microsoft Word
The all mechanism will match against everything, and in this case, the result will be a SoftFail for everything that gets to this point.
Spf Record Creator Microsoft
Further reading #
There are other mechanisms as well, but hopefully this post is enough to teach you the basics about SPF. The SPF project is a great resource and the section on record syntax goes into much more detail about the different parts of the SPF record.
Spf Record Generator Microsoft Office 2010
Keep an eye on the blog for more topics like this. I’ll have posts about DKIM and DMARC coming up. DMARC in particular has become much greater in relevance lately and SPF and DKIM are the building blocks that DMARC uses.
